Oracle APEX 系列文章11:全站启用 HTTPS,让你的 APEX 更安全
引言
钢哥的 Oracle APEX 系列文章:
- Oracle APEX 系列文章01:Oracle APEX, 让你秒变全栈开发的黑科技
- Oracle APEX 系列文章02:在阿里云上打造属于你自己的APEX完整开发环境 (安装 CentOS)
- Oracle APEX 系列文章03:在阿里云上打造属于你自己的APEX完整开发环境 (安装 Tomcat, Nginx)
- Oracle APEX 系列文章04:在阿里云上打造属于你自己的APEX完整开发环境 (安装XE, ORDS, APEX)
- Oracle APEX 系列文章05:在阿里云上打造属于你自己的APEX完整开发环境 (进一步优化)
- Oracle APEX 系列文章06:Oracle APEX 到底适不适合企业环境?
- Oracle APEX 系列文章07:Oracle APEX 18.1 新特性
- Oracle APEX 系列文章08:如何从 APEX 5.1.4 升级到 最新的 APEX 18.1
- Oracle APEX 系列文章09:为什么选择使用 Oracle APEX
- Oracle APEX 系列文章10:Oracle APEX Evangelion(EVA 补完计划)
- Oracle APEX 系列文章11:全站启用 HTTPS,让你的 APEX 更安全
- Oracle APEX 系列文章12:魔法秀,让你的 H5 页面秒变 APP
- Oracle APEX 系列文章13:Oracle APEX 入门基础资料整理
- Oracle APEX 系列文章14:Oracle APEX 18.1 Docker 镜像
- Oracle APEX 系列文章15:无人值守一键安装Oracle APEX环境
- Oracle APEX 系列文章16:AOP - PDF报表打印新选择
- Oracle APEX 系列文章17:如何利用 Oracle APEX 助力企业应用开发
目前主流的网站都要求 HTTPS 安全访问,Google Chrome 浏览器、微信内置浏览器打开非 HTTPS 的网页,都会提示不安全。如果做微信端开发,也是必须要 HTTPS 的网址才可以,可见 HTTPS 越来越重要了。
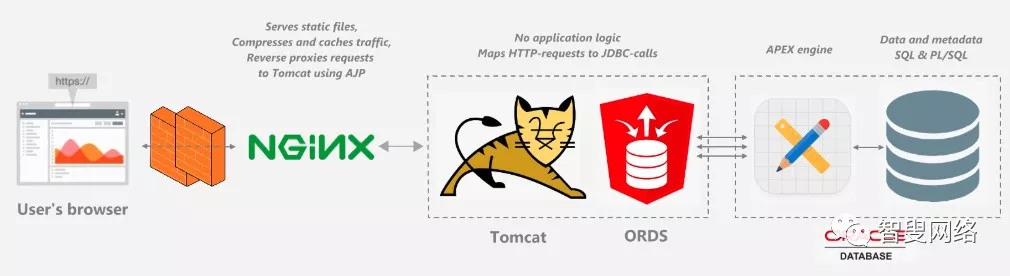
如果你按照钢哥之前的文章已经搭建好了 Oracle APEX 环境,那么你的应用架构应该如下图所示:

这里简单回顾一下各部分组件的作用:
- 用户在浏览器地址栏里输入URL,例如:https://apex.wangfanggang.com/ords/ (不要尝试打开这个网址了,我瞎写的)
- Nginx监听 HTTP (
80) 端口和 HTTPS (443) 端口,如果请求的是静态文件(如:image, js 或者 css),则直接获取/i/目录中的内容,对于其他动态请求(如:APEX请求),转发至后端 Tomcat 服务器做进一步处理。 - Tomcat 服务器接收到请求后,会查找部署在它上面的应用,就是我们之前部署的
ORDS应用; - 如果是 APEX 请求,ORDS 进一步将请求转发给 APEX (Oracle 数据库) 进行处理;如果是 ORDS 请求,自身进行处理;
原理比较简单,而我们要做的就是在 Nginx 层面将 HTTP 请求转发到 HTTPS 上,进而实现全站启用 HTTPS 访问。
申请 SSL 证书
这里以在阿里云上购买免费 SSL 证书为例,首先登录阿里云控制台,进入安全(云盾)-> SSL证书(应用安全),点击购买证书。
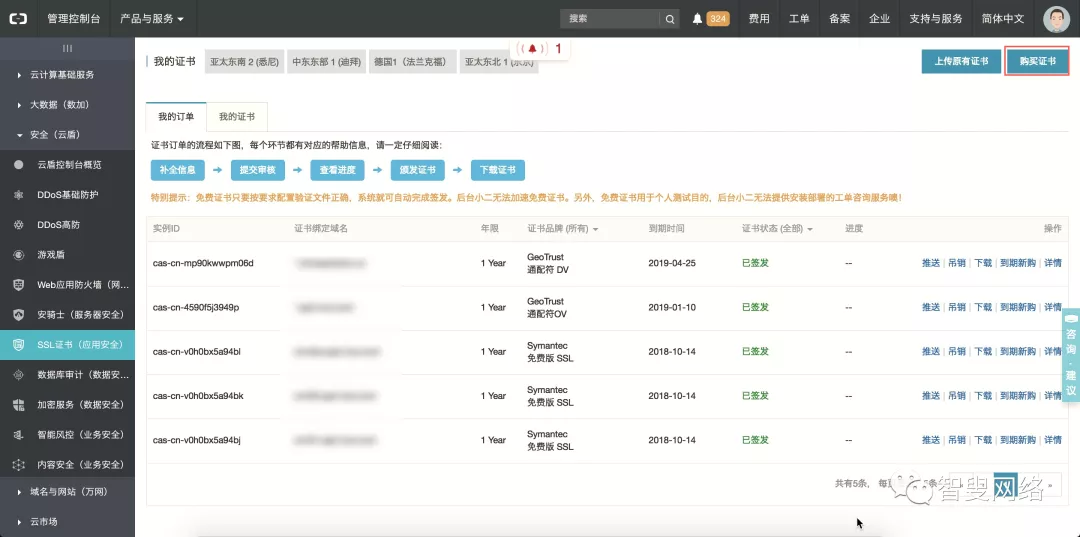
进入到选择购买页面,提示1年需要五千多大洋,土豪直接点击付款即可。
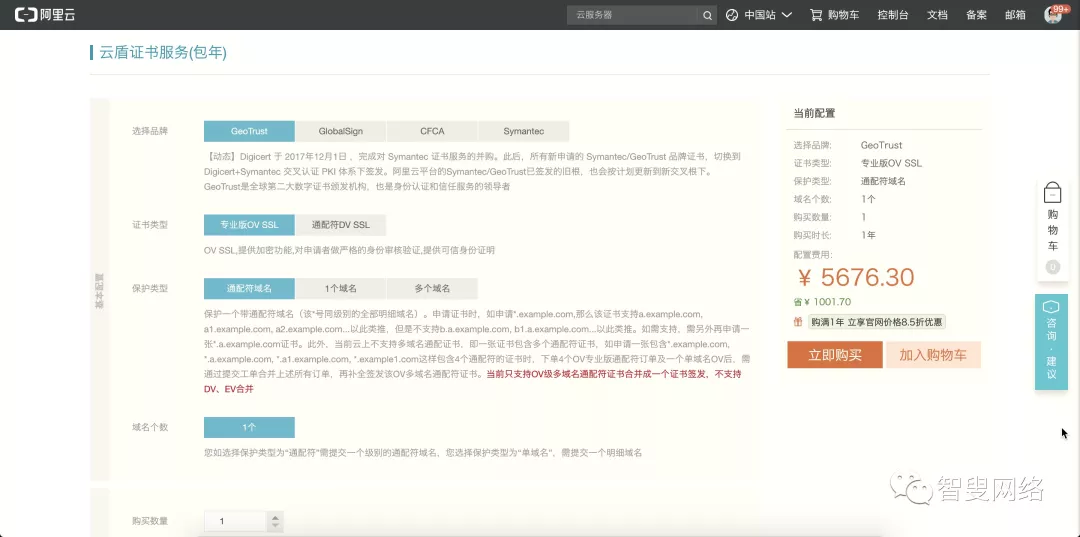
好吧,我是穷人,只能看看有没有免费证书。其实是有的,依次点击Symantec -> 1个域名 -> 免费型DV SSL,成功激活30人:)
接下来回到控制台,补全刚刚申请的证书信息。
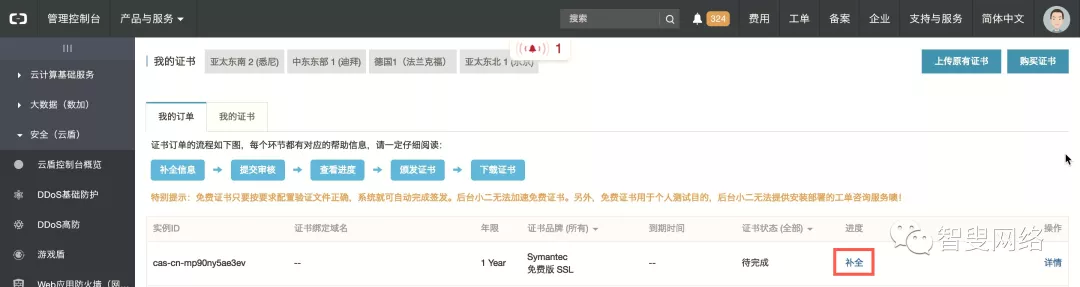
按照提示补全信息。
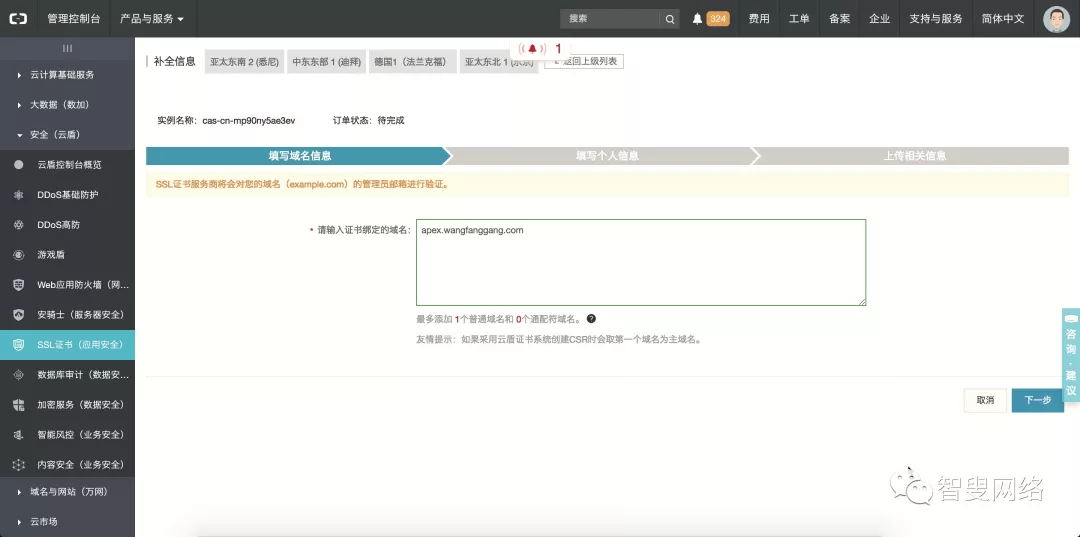
**钢哥提示:**由于我们申请的是阿里云的免费证书,只能作用于一个固定域名,一般我们都不会把主域名用来放置APEX应用,所以这里可以填写诸如:apex.xxx.com 的二级域名。如果你想要免费通配符域名,可以移步这里:使用Let’s Encrypt给网站加上免费HTTPS证书
另外需要注意的是,第二步的验证环节,如果你选择的是文件验证,请一定按照提示把对应的验证文件放到你的服务器上,
正常文件验证一般不会超过5分钟,如果长时间没验证通过,一定是你操作有问题了。
当你的证书申请通过后,就可以点击下载链接了。
配置 Nginx
将 SSL 证书添加进nginx.conf,按照下载证书页面的提示配置 Nginx:
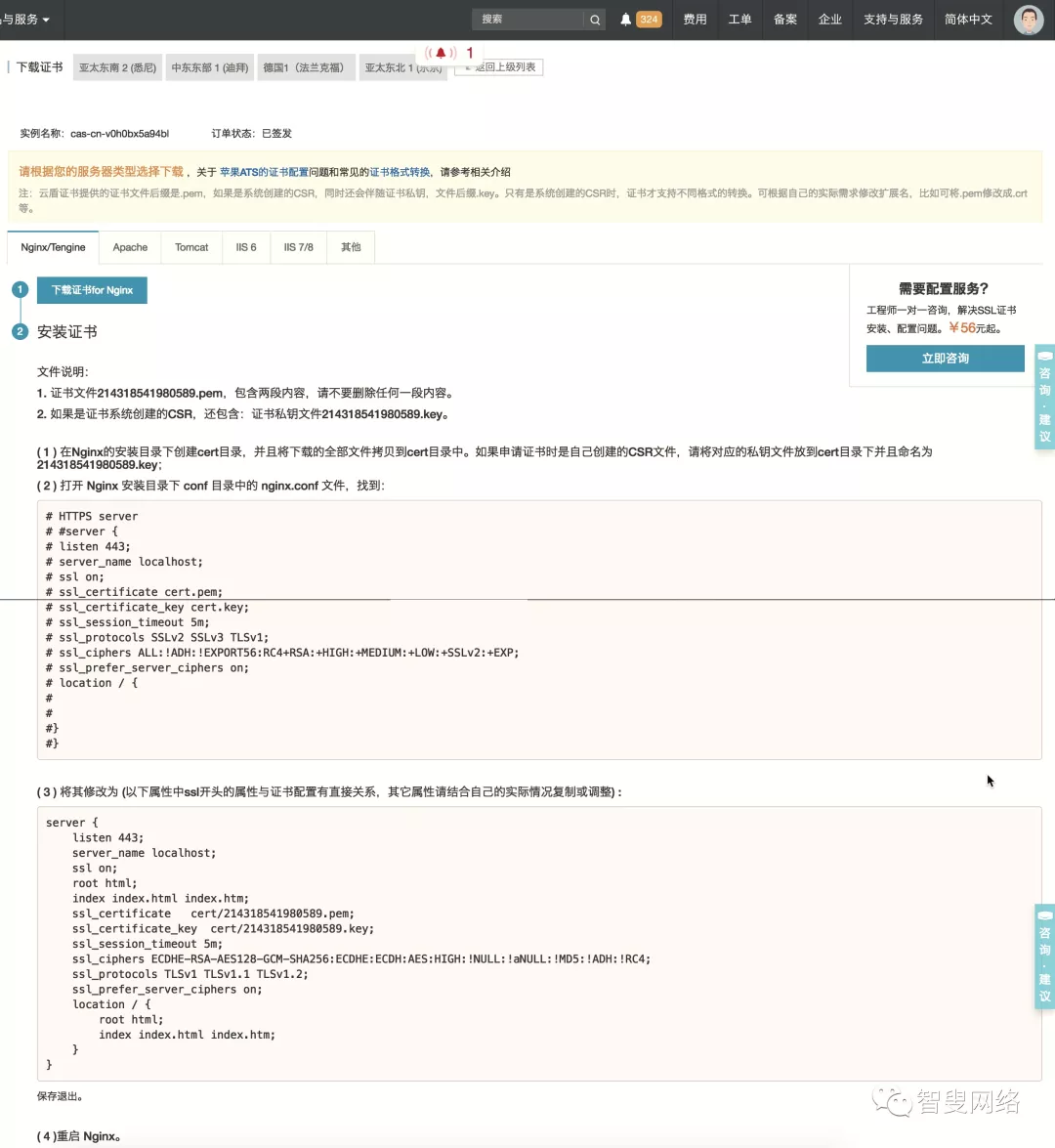
我的nginx.conf文件内容如下:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135worker_processes auto;
worker_rlimit_nofile 10000;
error_log logs/error.log;
events
{
worker_connections 2048;
#==告诉nginx收到一个新链接通知后接受尽可能多的链接
multi_accept on;
#==设置用于复用客户端线程的轮训方法
use epoll;
}
http
{
include mime.types;
default_type application/octet-stream;
charset UTF-8;
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /etc/nginx/logs/access_log.log main;
server_tokens off;
sendfile on;
tcp_nopush on;
keepalive_timeout 65;
proxy_connect_timeout 600;
proxy_send_timeout 600;
proxy_read_timeout 600;
send_timeout 600;
#==设置nginx采用gzip压缩的形式发送数据,减少发送数据量,但会增加请求处理时间及CPU处理时间,需要权衡
gzip on;
#==加vary给代理服务器使用,针对有的浏览器支持压缩,有个不支持,根据客户端的HTTP头来判断是否需要压缩
gzip_vary on;
gzip_http_version 1.0;
gzip_types text/plain application/javascript application/x-javascript text/css;
gzip_min_length 1024;
gzip_comp_level 3;
server
{ listen 443 default_server;
server_name apex.wangfanggang.com;
ssl on;
ssl_certificate cert/214412416080589.pem;
ssl_certificate_key cert/214412416080589.key;
ssl_session_timeout 5m;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
location = /
{
# 默认打开某个APEX应用
rewrite ^/(.*) https://apex.wangfanggang.com/ords/f?p=102 redirect;
}
location ~* \.(eot|ttf|woff|woff2)$
{
add_header Access-Control-Allow-Origin *;
}
location ^~ /i/
{
alias /u01/tomcat/webapps/i/;
}
location ^~ /ords/
{
# 将请求转发到tomcat上
proxy_pass http://localhost:8080/ords/;
proxy_redirect off;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
client_max_body_size 20m;
}
}
server
{
listen 80 default_server;
server_name apex.wangfanggang.com;
include /etc/nginx/default.d/*.conf;
location = /
{
# 所有http请求统一重定向到https上
rewrite ^/(.*) https://apex.wangfanggang.com/ords/f?p=102 redirect;
}
location ~* \.(eot|ttf|woff|woff2)$
{
add_header Access-Control-Allow-Origin *;
}
location ^~ /i/
{
alias /u01/tomcat/webapps/i/;
}
location ^~ /ords/
{
# 所有http请求统一重定向到https上
proxy_pass https://apex.wangfanggang.com/ords/;
proxy_redirect off;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
client_max_body_size 20m;
}
error_page 404 /404.html;
location = /40x.html
{
}
error_page 500 502 503 504 /50x.html;
location = /50x.html
{
}
}
}
配置完 nginx,别忘了重启令配置生效。再次在浏览器中访问 APEX 页面,如果能正常访问,恭喜你,你的 SSL 证书生效了!!
配置 Tomcat
钢哥在配置的时候 SSL 证书时遇到了一个奇怪的问题,就是启用 SSL 证书后,访问 APEX 页面时会发生重定向错误(302 error:too_many_redirects),导致无法正常访问。
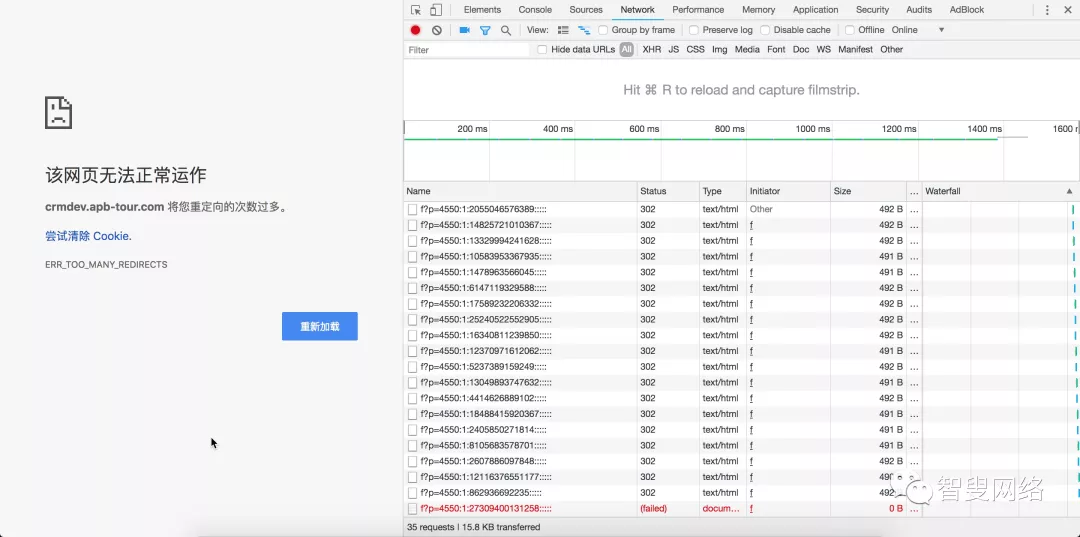
经过跟同事几天的研究,发现除了要在 Nginx 上启用 SSL 证书以外,还必须在 Tomcat 上也启用。还是回到阿里云控制台证书下载页面,找到 Tomcat 配置证书部分。
钢哥提示:特别要注意的是,这里要选择
JKS格式证书进行安装,否则会有问题。
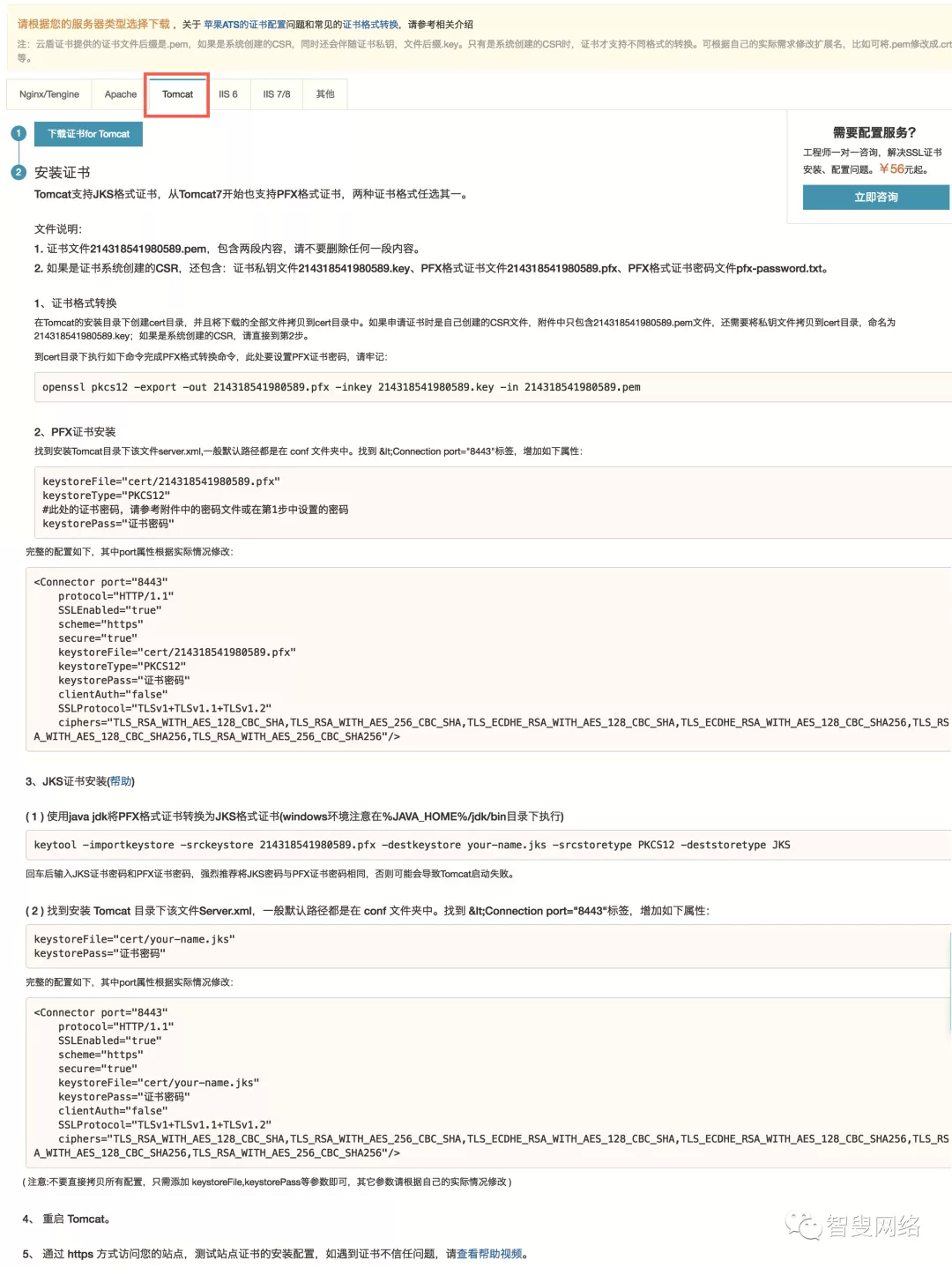
在 Tomcat 的server.xml文件中添加如下内容:1
2
3
4
5<Valve
className = "org.apache.catalina.valves.RemoteIpValve"
remoteIpHeader = "X-Forwarded-For"
protocolHeader = "X-Forwarded-Proto"
/>
我的server.xml文件内容:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<!--
Note: A "Server" is not itself a "Container", so you may not
define subcomponents such as "Valves" at this level.
Documentation at /docs/config/server.html
-->
<Server port="8005" shutdown="SHUTDOWN">
<Listener className="org.apache.catalina.startup.VersionLoggerListener"
/>
<!--
Security listener. Documentation at /docs/config/listeners.html
<Listener className="org.apache.catalina.security.SecurityListener"
/>
-->
<!--
APR library loader. Documentation at /docs/apr.html
-->
<Listener className="org.apache.catalina.core.AprLifecycleListener" SSLEngine="on"
/>
<!--
Prevent memory leaks due to use of particular java/javax APIs
-->
<Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener"
/>
<Listener className="org.apache.catalina.mbeans.GlobalResourcesLifecycleListener"
/>
<Listener className="org.apache.catalina.core.ThreadLocalLeakPreventionListener"
/>
<!--
Global JNDI resources
Documentation at /docs/jndi-resources-howto.html
-->
<GlobalNamingResources>
<!--
Editable user database that can also be used by
UserDatabaseRealm to authenticate users
-->
<Resource
name = "UserDatabase" auth="Container"
type = "org.apache.catalina.UserDatabase"
description = "User database that can be updated and saved"
factory = "org.apache.catalina.users.MemoryUserDatabaseFactory"
pathname = "conf/tomcat-users.xml"
/>
</GlobalNamingResources>
<!--
A "Service" is a collection of one or more "Connectors" that share
a single "Container" Note: A "Service" is not itself a "Container",
so you may not define subcomponents such as "Valves" at this level.
Documentation at /docs/config/service.html
-->
<Service
name = "Catalina">
<!--
The connectors can use a shared executor, you can define one or more named thread pools
-->
<!--
<Executor
name = "tomcatThreadPool"
namePrefix = "catalina-exec-"
maxThreads = "150"
minSpareThreads = "4"
/>
-->
<!--
A "Connector" represents an endpoint by which requests are received
and responses are returned. Documentation at :
Java HTTP Connector: /docs/config/http.html
Java AJP Connector: /docs/config/ajp.html
APR (HTTP/AJP) Connector: /docs/apr.html
Define a non-SSL/TLS HTTP/1.1 Connector on port 8080
-->
<Connector
port = "8080"
protocol = "HTTP/1.1"
connectionTimeout = "20000"
redirectPort = "8443"
/>
<!--
A "Connector" using the shared thread pool
-->
<!--
<Connector
executor = "tomcatThreadPool"
port="8080" protocol = "HTTP/1.1"
connectionTimeout = "20000"
redirectPort = "8443"
/>
-->
<!--
Define a SSL/TLS HTTP/1.1 Connector on port 8443
This connector uses the NIO implementation. The default
SSLImplementation will depend on the presence of the APR/native
library and the useOpenSSL attribute of the
AprLifecycleListener.
Either JSSE or OpenSSL style configuration may be used regardless of
the SSLImplementation selected. JSSE style configuration is used below.
-->
<!--
<Connector
port = "8443"
protocol = "org.apache.coyote.http11.Http11NioProtocol"
maxThreads = "150"
SSLEnabled = "true">
<Certificate
certificateKeystoreFile = "conf/localhost-rsa.jks"
type = "RSA"
/>
</Connector>
-->
<Connector
port="8443"
protocol = "HTTP/1.1"
SSLEnabled = "true"
scheme = "https"
secure = "true"
keystoreFile = "cert/214412416080589.jks"
keystorePass = "abc123"
clientAuth = "false"
SSLProtocol = "TLSv1+TLSv1.1+TLSv1.2"
ciphers = "TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA256"
/>
<!--
Define a SSL/TLS HTTP/1.1 Connector on port 8443 with HTTP/2
This connector uses the APR/native implementation which always uses
OpenSSL for TLS.
Either JSSE or OpenSSL style configuration may be used. OpenSSL style
configuration is used below.
-->
<!--
<Connector
port = "8443"
protocol = "org.apache.coyote.http11.Http11AprProtocol"
maxThreads = "150"
SSLEnabled = "true" >
<UpgradeProtocol
className="org.apache.coyote.http2.Http2Protocol"
/>
<SSLHostConfig>
<Certificate
certificateKeyFile = "conf/localhost-rsa-key.pem"
certificateFile = "conf/localhost-rsa-cert.pem"
certificateChainFile = "conf/localhost-rsa-chain.pem"
type = "RSA"
/>
</SSLHostConfig>
</Connector>
-->
<!--
Define an AJP 1.3 Connector on port 8009
-->
<Connector
port = "8009"
protocol = "AJP/1.3"
redirectPort = "8443"
/>
<!--
An Engine represents the entry point (within Catalina) that processes
every request. The Engine implementation for Tomcat stand alone
analyzes the HTTP headers included with the request, and passes them
on to the appropriate Host (virtual host).
Documentation at /docs/config/engine.html
-->
<!--
You should set jvmRoute to support load-balancing via AJP ie :
<Engine
name = "Catalina"
defaultHost = "localhost"
jvmRoute = "jvm1">
-->
<Engine
name = "Catalina"
defaultHost = "localhost">
<!--
For clustering, please take a look at documentation at:
/docs/cluster-howto.html (simple how to)
/docs/config/cluster.html (reference documentation)
-->
<!--
<Cluster className="org.apache.catalina.ha.tcp.SimpleTcpCluster"
/>
-->
<!--
Use the LockOutRealm to prevent attempts to guess user passwords
via a brute-force attack
-->
<Realm className="org.apache.catalina.realm.LockOutRealm">
<!--
This Realm uses the UserDatabase configured in the global JNDI
resources under the key "UserDatabase". Any edits
that are performed against this UserDatabase are immediately
available for use by the Realm.
-->
<Realm
className = "org.apache.catalina.realm.UserDatabaseRealm"
resourceName = "UserDatabase"
/>
</Realm>
<Host
name = "localhost"
appBase = "webapps"
unpackWARs = "true"
autoDeploy = "true">
<Valve
className = "org.apache.catalina.valves.RemoteIpValve"
remoteIpHeader = "X-Forwarded-For"
protocolHeader = "X-Forwarded-Proto"
/>
</Host>
</Engine>
</Service>
</Server>
重启 Tomcat 服务器,再次访问 APEX,烦人的重定向问题终于得以解决。
结语
用 HTTPS 协议来安全地访问你的 APEX 应用,这一点特别是对企业应用特别重要,相信你现在已经掌握了如何在 APEX 上全站启用 SSL 证书。本文如有遗漏或不足的地方也请随时跟钢哥交流,让我们共同学习,共同进步!